
Get in touch with our IT team.
How AMD EPYC makes your data more secure
Businesses today face a landscape of ever-evolving risks and threats, not only as cyber criminals get more sophisticated, but also as practices change to increased use of cloud service providers and hybrid working approaches. It is fair to say that as one security gap is closed, others are discovered and exploited. In most cases data as the main target of any attack - either attempting to steal it or disrupt access to it - so it is paramount that data is protected wherever it is found on the network and within any servers too. With this in mind, AMD EPYC 4th gen 9004, 8004 and 3rd gen 7003 processors feature a host of inbuilt security features that have increased and evolved over its several generations, that together can help mitigate these risks - we’ll look at each of these features and how, when combined, they make for the most secure server platforms available today.

Traditionally, data security has focussed on RAID and encryption, but this only addresses data at rest - data in flight across company networks and VPNs, and data is use within system memory, especially in virtualised environments - can be especially vulnerable. AMD EPYC processors are designed with a sophisticated suite of security technologies called AMD Infinity Guard that addresses these vulnerabilities to help improve data integrity. Firstly, Infinity Guard modernises with a multilayered approach to security and implement security features designed to be highly resistant to complex attacks, from BIOS manipulation to virtualised malicious hypervisor attacks. Infinity Guard also complements many server software applications and hardware solutions. Secondly, it establishes a strong foundation for platform security helping mitigate malware with the AMD EPYC hardware “root of trust”. Thirdly, Infinity Guard achieves full memory encryption to help protect against internal and physical attacks - data is encrypted even if memory is physically removed from the server. Next, confidential computing in virtualised environments is guaranteed as memory data is encrypted for each virtual machine. Lastly, Infinity Guard is designed for seamless x86 application support without having to modify code.
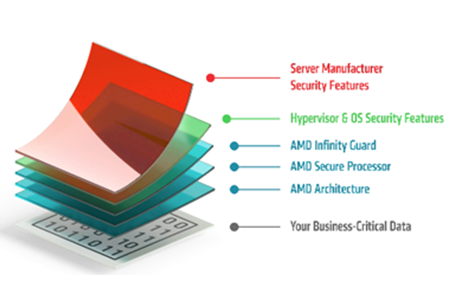
Security is underpinned at the silicon level with AMD Secure Processor technology featuring dedicated cores that authenticate the initial BIOS software boot without corruption, validate code before it is executed to help ensure data and application integrity. AMD Secure Boot extends the AMD silicon root of trust to help protect the system BIOS - helping the system establish an unbroken chain of trust from the BIOS to the OS Bootloader using UEFI, or Unified Extensible Firmware Interface, secure boot. This feature helps defend against remote attackers seeking to embed malware into firmware. In virtualised environments, it can also be used when cryptographically verifying the software stack loaded on a cloud server. This silicon-level security is further enhanced by additional layers provided by operating system and hypervisor.
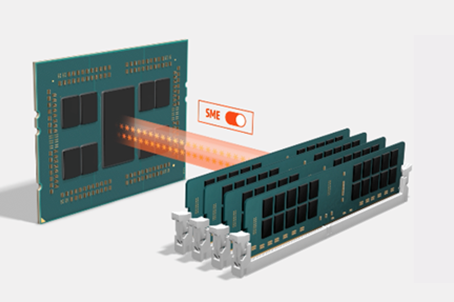
This is all backed-up by Secure Memory Encryption - by means of an 128-bit Advanced Encryption Standard, or AES, engine integrated into each of the eight memory controllers found in AMD EPYC processors. This helps protect against attacks on the integrity of main memory - such as cold-boot attacks - because it encrypts the data without modifications to application software. This high-performance encryption integrated into the memory channels also helps speed performance.
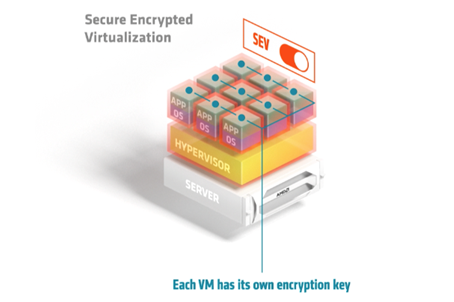
For virtualised or containerised environments, a feature called Secure Encrypted Virtualisation, or SEV, within AMD EPYC processors helps safeguard privacy and integrity by encrypting each virtual machine or container with one of up to 509 unique encryption keys known only to the AMD Secure Processor. This 128-bit AES encryption aids in protecting confidentiality of your data even if a malicious virtual machine finds a way into your virtual machine’s memory, or a compromised hypervisor reaches into a guest virtual machine.
Further related features combine with SEV to create strong, multilayer protection for data in use. When enabled, SEV-Encrypted State, or SEV-ES, helps prevent the hypervisor from seeing data actively being used by a virtual machine. Meanwhile SEV-Secure Nested Paging, or SEV-SNP, adds strong memory integrity protection capabilities to help prevent malicious hypervisor-based attacks, such as data replay and memory re-mapping, to create an isolated execution environment. It achieves this through attestation, providing proof that a particular virtual machine has write access to the memory – an important protection feature in virtual environments where multiple guests have access to the shared system memory. On top of the BIOS and memory encryption, AMD Shadow Stack provides hardware-enforced stack protection capabilities to help guard against malware attacks. This security feature addresses threat vectors such as return oriented programming, or ROP, attacks. It helps by keeping a record of the return addresses so a comparison can be made to ensure integrity is not compromised. Additionally AMD Shadow Stack enables Microsoft hardware enforced stack protection.
It is clear to see the multi-layered approach AMD has taken to server security, however it is worth mentioning why this is becoming such a critical consideration. It is hard to think of any industry where data security and integrity shouldn’t be the priority driver - healthcare providers are required to defend patient records against unauthorised access; financial organisations must mitigate the risk of disclosure or alteration of financial data; the retail sector is expected to secure customer data and transactions; whilst manufacturing needs to automate and migrate confidently across on-premise and cloud infrastructures. Whatever your industry sector it is worth validating the security performance of your existing servers - are you satisfied with the integrity of your most critical data? Maybe it is time to consider a fully customisable 3XS server solution based on AMD 3rd or 4th gen EPYC processors - our team of system architects can work with you to spec and build the perfect machine for your organisation.
